Understanding iCloud Activation Lock and its Implications
iCloud Activation Lock is a security feature designed to protect your iPhone, iPad, or Mac from unauthorized access if lost or stolen. It requires your Apple ID and password to reactivate the device after a factory reset. While a crucial security measure, Activation Lock can become a significant hurdle if you lose access to your Apple ID or purchase a used device without proper authorization. This guide explores methods to bypass Activation Lock, but it's crucial to understand that unauthorized bypass attempts carry significant legal and security risks. We will emphasize responsible disclosure and user safety throughout.
Methods for Bypassing iCloud Activation Lock: An Informed Approach
Several methods exist for attempting to bypass iCloud Activation Lock, each with varying degrees of effectiveness, security risks, and legal implications. Let's examine them:
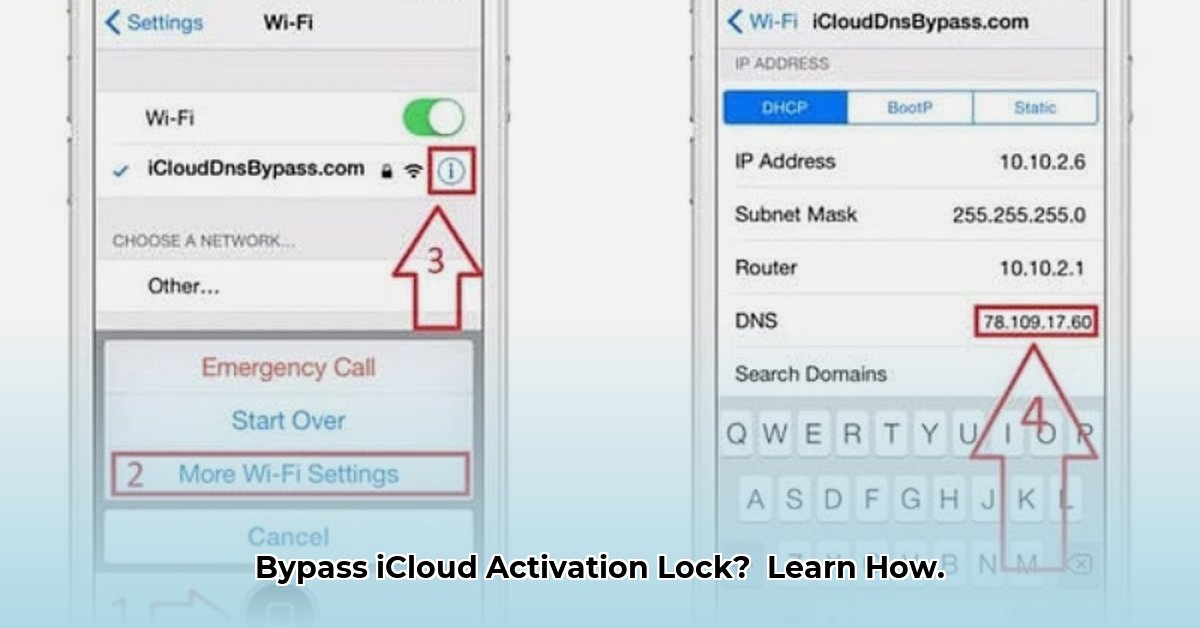
1. DNS Bypass: A Limited and Unreliable Technique
The DNS bypass method involves modifying your device's DNS settings to attempt to circumvent the Activation Lock screen. Think of it as a temporary workaround, offering only limited access and potentially causing temporary functionality. This method's effectiveness is highly variable and depends on the device's iOS version and the specific DNS server used. It's often described as a "peek" rather than a complete solution.
- How it works (at a high level): It attempts to spoof the activation server's address.
- Effectiveness: Low success rate; often temporary and unreliable.
- Security Risks: Minimal direct security risk, but potential for vulnerabilities if paired with malicious software.
- Legal Risks: Generally low, as it doesn't directly involve altering the device's core functionality.
2. IMEI Unlocking: A High-Risk, High-Reward Approach
IMEI unlocking involves modifying the device's unique identifier (IMEI number) to attempt to disable Activation Lock. This method represents a more aggressive approach with potentially high rewards but carries significant risks. This is akin to using a master key to bypass a security system.
- How it works (at a high level): It attempts to alter the device's identity, making it appear as if Activation Lock isn't applied.
- Effectiveness: Potentially high, but success is not guaranteed and depends on the provider and device.
- Security Risks: Moderate to high, as unauthorized modifications can compromise device security.
- Legal Risks: High; unauthorized IMEI modification is illegal in many jurisdictions and can result in serious penalties.
3. Third-Party Software: A Minefield of Malware and Scams
Numerous third-party software programs claim to bypass iCloud Activation Lock. However, a significant percentage of these are scams designed to steal your information or install malware on your device. Their effectiveness is highly questionable, and the risks far outweigh any potential benefits. Downloading and using such software is extremely risky. This analogy demonstrates significant risk: you are walking into a minefield.
- How it works (at a high level): These programs generally claim to exploit vulnerabilities in the Activation Lock system; however, their methods are often unclear and unreliable.
- Effectiveness: Unreliable; often ineffective and potentially harmful.
- Security Risks: Very high; significant risk of malware infection, data loss, and identity theft.
- Legal Risks: High; using unauthorized software to bypass security measures is often illegal.
Risk Assessment Comparison: Choosing Your Path Carefully
The following table summarizes the risks and rewards of each method:
| Method | Effectiveness | Security Risk | Legal Risk | Cost |
|---|---|---|---|---|
| DNS Bypass | Low | Low | Low | Free |
| IMEI Unlock Service | High | Moderate | High | High |
| Unverified Software | Very Low | Very High | Very High | Variable |
Safer Alternatives and Best Practices
Before considering any risky bypass methods, explore legitimate alternatives:
- Contact Apple Support: If you legitimately own the device, Apple Support might be able to help resolve the issue.
- Contact the Previous Owner: If you purchased a used device, contact the previous owner to obtain the necessary Apple ID and password information.
- Official Unlocking Services (if available): In some specific circumstances, Apple or authorized providers may offer official unlocking services. This is the safest option if available.
- Data Backups: Regularly back up your data to prevent loss in case of any complications.
Remember: Prioritizing data security and adhering to legal practices is vital. Bypassing security measures without authorization carries serious consequences.
Conclusion: Responsible Device Management
This guide has explored several methods of potentially bypassing iCloud Activation Lock. However, we strongly advise against employing methods with high legal or security risks. Prioritizing safe and legal practices, including contacting Apple Support or the previous owner, is always the preferred approach. Unauthorized access is dangerous and illegal, and its potential consequences should be considered seriously. The information provided is for educational purposes only and should not be interpreted as encouragement for illegal activity.